Introduction
In the ever-evolving world of cybersecurity, staying ahead of potential threats is not just important — it's essential. And when it comes to building effective, powerful, and flexible tools for ethical hacking, Python is the programming language of choice for countless professionals around the globe.
Why Python? Because it’s simple, versatile, and incredibly effective at automating complex security tasks. Whether you're scanning networks, performing penetration testing, or analyzing malware, Python provides the foundational strength needed to explore, exploit, and reinforce digital systems — legally and ethically.
But here’s the thing: while tools matter, having the right IT partner is what truly makes a difference in this space.
Introducing True Value Infosoft, the best app development company in India and a leader in digital transformation and enterprise-grade solutions. As the best IT company trusted by startups, enterprises, and governments alike, True Value Infosoft offers cutting-edge development services with expertise in cybersecurity and ethical hacking.
This guide dives deep into how Python is being used in the realm of cybersecurity — specifically in ethical hacking. We’ll walk you through the fundamentals, real-world applications, key benefits, and why every aspiring cybersecurity expert should master Python.
Let’s explore the future of ethical hacking — one Python script at a time.
Understanding Ethical Hacking and Its Importance
Ethical hacking refers to the practice of intentionally probing and testing systems to identify vulnerabilities — with permission. It is a legal and structured activity that mimics the actions of malicious hackers, but with the goal of strengthening security rather than breaking it.
Why Ethical Hacking Is Crucial:
- Proactive Defense: It allows organizations to detect and fix vulnerabilities before attackers exploit them.
- Regulatory Compliance: Many standards like GDPR, HIPAA, and ISO 27001 require security testing.
- Risk Mitigation: Identifies potential attack vectors and reduces the risk of data breaches.
- Trust and Reputation: Businesses that invest in ethical hacking demonstrate a commitment to data protection.
Python stands out as the go-to language for ethical hackers, thanks to its readability and massive ecosystem of libraries and frameworks.
Why Python is the Top Language for Ethical Hackers
Python's dominance in cybersecurity is no accident. It’s a powerful, versatile language that simplifies complex tasks and enhances productivity.
Key Reasons Ethical Hackers Love Python:
- Easy Syntax: Readable, clean, and beginner-friendly.
- Wide Range of Libraries: From networking to web scraping and automation, Python has it all.
- Cross-platform Support: Works on Windows, Linux, and macOS without modifications.
- Strong Community Support: Thousands of tutorials, tools, and frameworks available.
- Integration Capabilities: Easily integrates with other tools, APIs, and third-party services.
Python serves as a launchpad for rapid development of custom security tools, making it ideal for everything from reconnaissance to reporting.
Common Ethical Hacking Tasks You Can Do with Python
Python empowers ethical hackers to automate and scale a wide variety of security-related tasks.
1. Information Gathering
- Perform OSINT (Open Source Intelligence)
- Gather metadata from files, websites, and emails
- Scan for open ports and services
2. Vulnerability Scanning
- Automate detection of known CVEs
- Integrate with security APIs to assess systems
- Simulate common attack patterns
3. Network Analysis
- Monitor real-time traffic
- Detect suspicious behavior and packet anomalies
- Perform ARP spoofing and sniffing (ethically, in lab environments)
4. Web Application Testing
- Identify XSS, SQLi, and CSRF vulnerabilities
- Crawl and analyze websites
- Perform directory brute-forcing
5. Password Cracking and Credential Testing
- Brute-force passwords (in a controlled environment)
- Test password policies
- Simulate dictionary attacks using ethical methods
6. Wireless Attacks Simulation
- Scan for Wi-Fi networks
- De-authenticate clients
- Test encryption standards (WEP, WPA2)
7. Malware Analysis and Reverse Engineering
- Analyze logs for indicators of compromise
- Examine malware behavior in sandboxes
- Automate reporting and threat analysis
The Power of Python Libraries in Cybersecurity
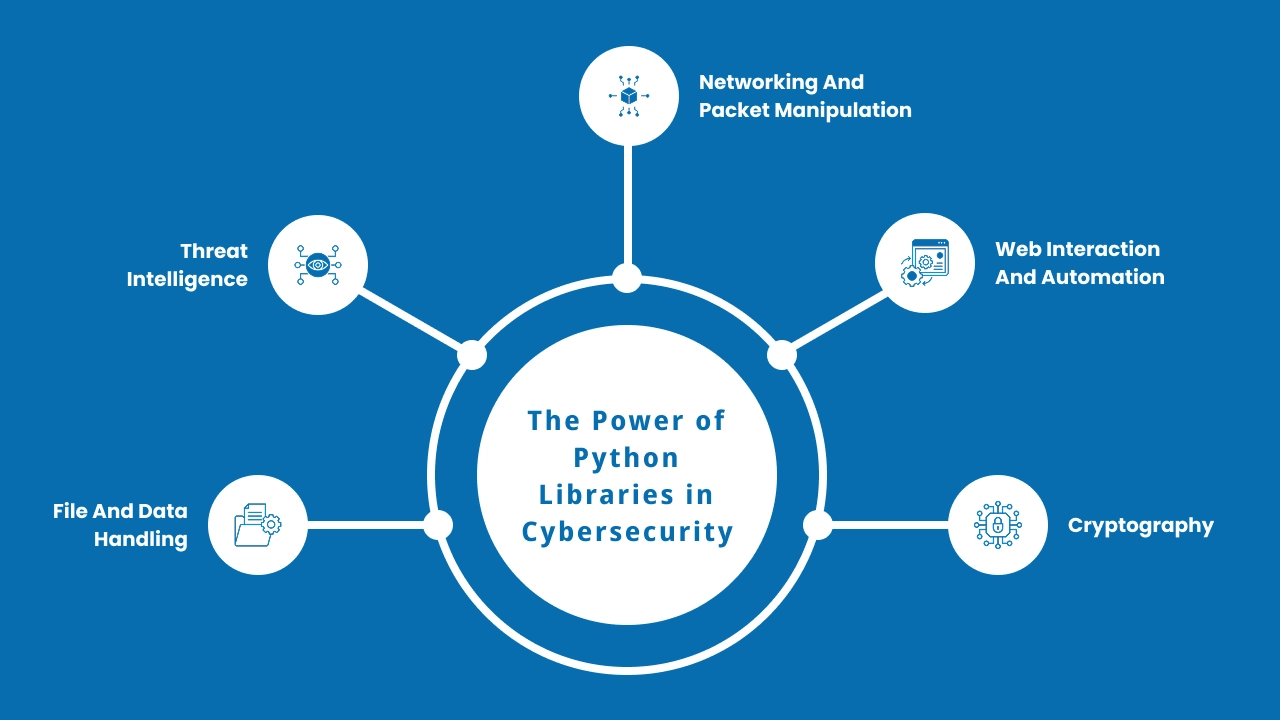
Python’s power lies in its ecosystem. Here’s how different libraries are used by cybersecurity professionals:
1. Networking and Packet Manipulation
- Capture, analyze, and manipulate network traffic
- Automate scanning tools and penetration testing scripts
2. Web Interaction and Automation
- Simulate login attempts
- Automate form submissions
- Scrape security headers from websites
3. Cryptography
- Secure sensitive data
- Generate and validate encryption keys
- Analyze encryption algorithms
4. File and Data Handling
- Analyze logs, configs, and binary files
- Create structured reports
- Parse and visualize large data sets
5. Threat Intelligence
- Consume threat feeds
- Monitor domains and IPs in real-time
- Alert on suspicious changes or indicators
True Value Infosoft’s cybersecurity experts leverage these Python libraries daily to test enterprise systems and ensure data protection for clients globally.
Python and Penetration Testing – A Perfect Match
Penetration testing, or "pen testing," involves simulating cyberattacks to evaluate a system’s defense.
Why Python Is Perfect for This Role:
- Rapid script development for unique scenarios
- Automation of repetitive tasks like scanning and data collection
- Easily customizable testing workflows
- Integration with Metasploit, Nmap, and other tools
Python scripts can form the backbone of pen testing frameworks, offering flexibility that GUI-based tools can't match.
Ethical Hacking Tools Built with Python
Some of the most effective ethical hacking tools have Python under the hood. While we won’t delve into coding, here’s how they contribute:
- Port scanners: Rapidly scan systems for open ports.
- Credential testers: Simulate brute-force attacks (ethically).
- Packet sniffers: Capture traffic for analysis.
- Web scanners: Detect common web app flaws.
- Custom exploits: Craft unique attack simulations for testing.
These tools are often tailored for in-house use by professional cybersecurity teams, such as those at True Value Infosoft.
How Ethical Hackers Build a Python Workflow
A successful ethical hacker using Python typically follows a structured workflow:
- Target Identification
- Collect IPs, domains, and app URLs
- Reconnaissance
- Gather intel through scanning and OSINT
- Exploitation Simulation
- Attempt access using automated scripts
- Privilege Escalation Testing
- Simulate lateral movement
- Reporting and Recommendations
- Present findings and mitigation steps
Python streamlines every step, allowing security pros to stay agile and proactive.
Learning Python for Cybersecurity
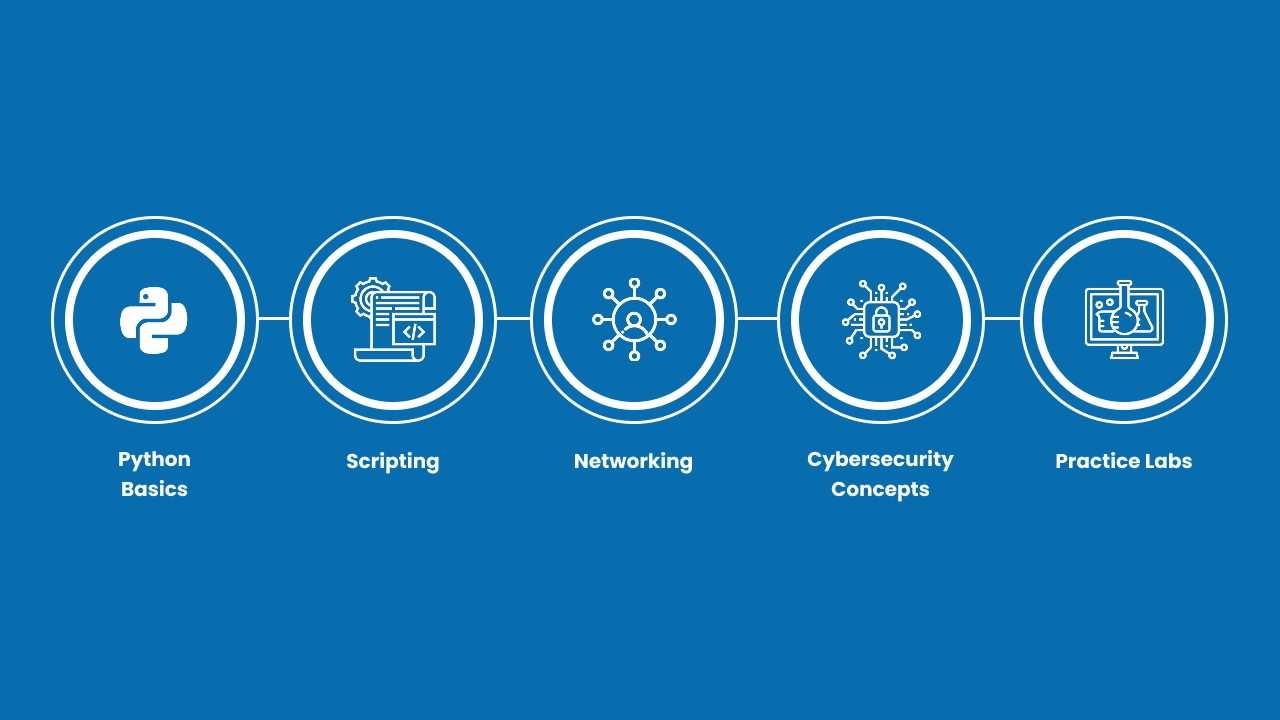
Getting started with Python for cybersecurity doesn’t require prior experience with programming. Here’s a learning roadmap:
- Python Basics: Learn syntax, data types, and logic flow.
- Scripting: Write automation scripts to perform tasks.
- Networking: Understand protocols like TCP/IP and HTTP.
- Cybersecurity Concepts: Study ethical hacking frameworks, OWASP Top 10, and penetration testing methodologies.
- Practice Labs: Use virtual machines and capture-the-flag (CTF) challenges to sharpen your skills.
At True Value Infosoft., we train our cybersecurity teams using custom-built Python challenges that simulate real-world threat scenarios — giving them a hands-on edge.
Real-World Use Cases of Python in Cybersecurity
Python isn’t just theoretical — it’s used actively in top cybersecurity operations.
Case Study Examples:
- Enterprise Security: Automating log analysis to detect potential breaches.
- Banking Sector: Testing customer-facing web apps for compliance vulnerabilities.
- Healthcare: Protecting sensitive patient records through encryption analysis.
- Government: Simulating state-level cyberattacks for preparedness drills.
True Value Infosoft has deployed Python-based security tools in these environments with remarkable success — ensuring systems are secure, scalable, and future-proof.
Challenges of Using Python in Cybersecurity
While Python is powerful, it's not without limitations:
- Performance: Slower than compiled languages like C/C++
- Distribution: Scripts can be reverse-engineered if not obfuscated
- Dependency Management: Keeping libraries up-to-date is crucial
- Legal Risks: Misuse of scripts can lead to legal issues without proper authorization
That’s why ethical hacking should always be conducted with permission and guided by legal compliance — something True Value Infosoft strictly adheres to in every engagement.
Conclusion
Python has emerged as the unsung hero of ethical hacking — combining simplicity, flexibility, and power in one cohesive language. Its role in cybersecurity is only growing, especially as threats become more sophisticated and defenders must adapt quickly.
By mastering Python, ethical hackers can build custom tools, automate complex workflows, and deliver high-impact security insights to clients and organizations.
Whether you’re just starting out or already navigating the cybersecurity landscape, Python offers a career-defining advantage.
And when you’re ready to take it to the next level, True Value Infosoft — the best app development company in India and a pioneer in secure IT solutions — is here to support your journey.
Let’s build a safer digital world, together.
FAQs
Python is a great start and can take you far in ethical hacking. However, a successful ethical hacker also needs knowledge of networks, operating systems, and security principles.
Yes, Python’s beginner-friendly syntax makes it one of the best first languages for cybersecurity professionals. Many people start from scratch and quickly learn to build tools and automate tasks.
Python is used for tasks such as scanning networks, simulating attacks, automating vulnerability assessments, parsing logs, and scripting custom security tests.
Using Python for hacking is legal only when it's done ethically — with permission and within the scope of authorized testing. Unauthorized access or scanning is illegal and punishable.
Absolutely. True Value Infosoft offers full-cycle cybersecurity solutions, including ethical hacking, vulnerability assessment, and Python-powered security automation. We’re your trusted partner in building secure digital platforms.